The Ultimate Guide on How to protect your PC from computer invaders
The Ultimate Guide on How to protect your PC from computer invaders

he internet and being online is one of, if not THE, ultimate resources for everyone in today's modern and dare we say it, digital world.
We use it for everything! To communicate with others, to carry out research, to work, to shop, to play etc. - when it comes to the internet the list could go on and on.
It's convenient; it's there at the tip of our fingers, and now with wi-fi hotspots, we’re never really without a connection!
However, we’re also now much more vulnerable to identity theft as well as invasion of privacy.
We leave digital footprints everywhere and putting your data in the wrong place, or the wrong hands can prove extremely costly, to you.
This guide highlights the cyber crimes you need to be aware of, the common challenges that we find ourselves facing daily, and how we can overcome these challenges by making some simple adjustments to how we view and use the internet and its different platforms.
Table of Contents
1. You are not safe online!

Computer invaders don't go away; they just change focus and adapt their attacks to target and break even the most powerful firewalls and antivirus!
1a) Common threats
Some of the most dominant and well-known cyber threats currently out there include:
Ransomware and Malware both used as a tool to carry our targeted threats, infecting computer systems as they go, and costing customers highly.
Data breaches are still one of the most important threats of today. Stealing personal information or company-wide information can lead to identity theft and fraud.
With business data most commonly found to be used for blackmail purposes or indeed to sell on for money.
Distributed Denial of Service attacks (DDoS) - these attacks are driven not only by financial gain, but also by political, ideological, or just bad opinion.
Payment card fraud - be aware of fake companies that show up at the point of sales online to abuse certain transactions, taking advantage of your personal information.
Crypto jacking – linked with cryptocurrency, crypto jacking attacks aim to exploit a computer user's bandwidth and processing power to mine for cryptocurrency. Such attacks can cripple a victim's system by manipulating their processing power.
Phishing emails – the most common form of threats and attacks due to their realism. Phishing emails set out to obtain personal data, hijack accounts, steal identities, carry out malicious activity from your PC and more!
SPAM – spam is often used to gain access to very targeted networks.
1b) Their effects on a PC
The effects all of these threats have on your PC or computer network can be fatal, fatal for the computer.
Depending on the security you have in place, as well as the type of virus/malware, and the expertise of your IT team, it will all depend on whether the hack and virus can be completely removed before any further damage is done.
Making operating systems run much slower than they should or stop working completely is just one effect these types of attacks can have on a computer.
That and all your files can be encrypted and used to access sensitive or personal information, or worse, your computer can be used to do bad things without you even knowing it's going on.
Your computer might also crash regularly, continuously show pop-up error messages, and create problems when trying to connect to secure networks.
This last point is very important for remote employees, because using their personal computers at home, which may be hacked or infected in some way, to log in to their office's private server, can open up more doors for intruders to gain access to!
1c) Staying safe
There are several ways to increase your security online. These include:
Reviewing your online activities – what sites are you shopping on? What content are you posting, and where are you posting this? How safe are the sites you are visiting?
Install the latest antivirus software and firewalls. With free and paid for protection now available, there is no excuse not to protect your PC. (SonicWall online is a great place to help you get started).
Make sure to use a personal private network. This will not only help your antivirus software to further protect your online privacy, but it will also help to hide IP addresses, protect passwords, and keep you anonymous online.
Be aware of the information you share on social media. Especially Facebook, whose business model is designed on using your personal information for advertising and marketing purposes.
Only use secure shopping sites
Use strong passwords (you will read this point a lot throughout this guide)
Delete or clear your tracking cookies. Deleting your online activity means it's harder to follow you and collect personal information about you.
2. Attack of the invaders
With global cybercrime damages predicted to reach $6 billion in costs (annually) by 2021, the online threat is not only real, but it is also continually evolving.
2a) Cybercrime at its worst - stats, history, and challenges to overcome
The second most investigated crime accounting for 50% of crimes in the UK is Cybercrime.
Hackers are invading PCs on average every 39 seconds!
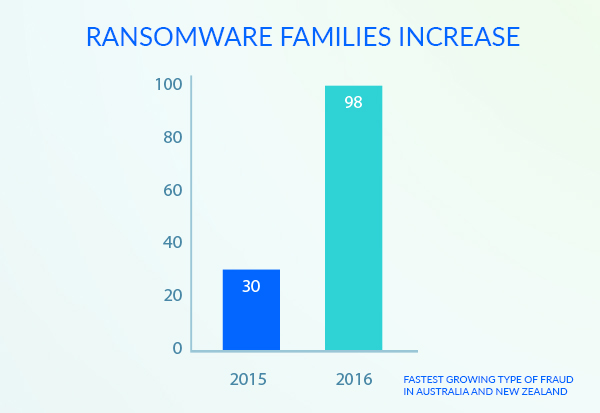
The number of ransomware families has increased from 30 in 2015 to 98 in 2016, with the demand also increasing from $294 in 2015 to £1,077 in 2016.
Records lost to hacking in 2017 stood at an average of 780,000 per day.
2015/16 saw identity takeover become the fastest growing type of fraud in Australia and New Zealand.
In the past year, nearly 200 million people across 21 different countries experienced some form of cybercrime!
The cost of online crime and activity is real:
- The cost of data breaches annually now stands at a staggering $2.1 trillion.
- In 2017, the total revenue coaxed out of people and businesses from cybercriminals worldwide stood at $1.5 trillion!
- $3.8 million, is the cost of data breaches to businesses (on average).
- $600 billion the global cost of cybercrime in 2017.
Challenges come in many shapes and sizes
Take, for example, the recent hacking of Facebook user accounts. Affecting nearly 50 million users worldwide, over 14 million people had their location and search history exposed for all to see!
On this occasion users of the site did nothing wrong and nor was there anything they could do to stop or pre-empt this from happening (besides not having a Facebook account at all), because the hackers took advantage of a Facebook privacy feature, which allowed them to access users' accounts without them knowing.
Now, as one of the largest data breaches in Facebook's history, the company's engineers are working to fix the problem and have advised another 40 million users to log out of their accounts as a precaution. Logging out and logging back in, allowed Facebook to reset users access tokens, protecting their accounts.
Further investigations are still ongoing to the extent of how these bugs can be rectified.
This type of breach is not uncommon as we look further into cybercrime and in particular. WikiLeaks, who released over 8,000 CIA documents (of course classified) in 2017. A team of hackers also released sensitive emails from French presidential candidate Emmanuel Macron in the same year.
Mobile platforms are the fastest growing target areas for hackers, with 80% of mobile fraud carried out through mobile apps and 60% of online fraud carried out through mobile platforms.
These attacks are not only real, but they're big!
3. Keep your computer safe

With online threats at an all-time high, we've compiled a list of top tips to protect you and your computer from computer invaders.
Without needing to install a thing:
- Avoid sites which you don't trust or don't look 100% genuine.
- Don't open emails from unknown/not trusted senders
- Don't open attachments from just anyone!
- Take your passwords more seriously! With more than 60% of people using the same password across multiple sites, make sure you use longer passwords. Use a combination of lower and upper case, numbers, and characters. Avoid obvious ones such as children's birthdays!
- Check your security settings in your browser. Reviewing and setting these at the level that you need and want, you can block pop-ups and irrelevant ads, you can tell websites not to track your location and movements.
- Network security – disabling autorun on Windows, for example, can stop up to 50% of malware threats!
- Wi-Fi security at home – make sure to change your router's default settings by enabling a non-default password and network name.
- Wi-Fi security, public disable sharing and make sure to use a virtual private network (VPN) to secure your data and hide your IP address.
The need for software installation:
- Install the right firewalls and antivirus software depending on your needs and configuration settings required. Also, make sure to keep your firewall turned on!
- Keep your Windows operating system up to date, checking for the latest security updates and patches. Make sure you turn on the automatic update feature.
- Install antivirus and anti-spyware software. Providing real-time protection, helping to identify and block any unwanted mail and threats.
- Look to invest in cloud software or external hard drives, backup your folders regularly, and make sure you have a backup plan if the worst were to happen.
4. Firewalls
Most firewalls, over the years, have been developed in response to a security threat received. Action was then taken to develop and produce more advanced firewall technology to stop the threat from happening again.
4a) How they work
When we think of firewalls, we need to think of them as invisible walls, in both directions, that monitor everything that passes through them. If a threat is found, the wall will not allow it to pass through.
A firewall will ultimately stop hackers from accessing your computer via Wi-Fi connections and the internet and can help in two ways:
- It can allow traffic to pass through, except for data that meets a predetermined set of criteria.
- It can stop all traffic unless it meets a predetermined set of criteria.
Firewalls are a piece of security software that keeps track of the traffic to and from your computer. They are the first line of defence to protect your data and any important information.
4b) Why do you need them?
It is this misuse of confidential information and stealing of personal data which is why we need firewalls.
For example, hackers use Trojan viruses and key logging software to access computers and data. Things like passwords, bank details can all be taken and used without you realising for days (if not longer), racking up huge bills in your name as they go.
They can also use your computer against you, taking complete control without you knowing, and using it to run illegal activities online, or it's affecting the system in any way.
Firewalls and upgraded firewalls like SonicWall firewalls help to stop this from happening, placing a barrier between you and the hackers.
4c) Best Practice
Firewall best practice when it comes to business is to install complex firewall software to protect the most extensive networks, so that such security measures can be managed by a team.
Helping to:
- Prevent staff from sending certain types of emails or transmitting sensitive information.
- Stop employees accessing certain sites
- Prevent outside computers accessing computers inside the network
- Provide a variety of configurations
When it comes to firewalls for personal use, we recommend keeping it simple. The primary goal is to protect your computer and private network from malicious activity.
5. Antivirus software

Anti-virus software, in its purest form, protects against different types of malware, protecting your PC and your personal information.
5a) How they work
Good antivirus software helps to block everyday threats by finding them before they reach your computer, and before they reach you directly, pulling them away, and locking them in a safe place.
Anti-virus software is similar to anti-spy software in that it provides real-time protection (if you make sure to keep it updated regularly). Scanning all incoming information and blocking any unwanted information or threats which it detects.
5b) Why do you need them?
Malware and malicious software attacking our PCs are one of the biggest online threats.A virus of any kind can be spread over the internet and through email, quickly causing damage to your computer and files.
Malware in this sense also includes Trojan Horse programmes and spyware; all used to acquire your personal information for identity theft and fraud.
The right antivirus software will help to prevent spyware and malware from getting onto your computer and invading your privacy, but it is important to set up and use a secure password. Using long passwords including a combination of numbers, special characters, and upper- and lower-case letters is most recommended.
5c) Differences between firewalls and antivirus software
Both developed to offer you and your PC increased security, the key differences between antivirus software and firewalls are:
- Anti-virus can only be implemented in software, whereas a firewall can be both hardware and software.
- Anti-virus performs continuous scans on the PC in question, detecting, identifying and removing any threats found, whereas firewalls monitor and filter incoming and outgoing information.
- Anti-virus software can deal with external and internal attacks, while firewalls can only deal with external.
- You can apply set rules to firewalls for monitoring and securing PCs and networks; this is not possible with an antiantivirus that will run regular checks to see if programs or files are dangerous.
- A firewall can prevent untrusted and unauthorised applications from gaining access to your computer, but it does not do anything about it. Antivirus programs do this for you.
6. Email Security Software

When it comes to protecting your PC and computer systems, you need to make sure to invest in the right security software for you and your PC. However, you also need to bear in mind the need to defend yourself against all known and emerging viruses and hacks.
6a) Integrated email security software
Attacks are getting more and more advanced and varied, and for this reason, integrated email security software should be chosen instead of managing a number of different software systems.
Making life easier An integrated platform means you can manage, control and contain everything through one application. You can monitor all incoming and outgoing activity quickly and efficiently, and you can have a bird's eye view of the security of your PC.
Managing multiple applications is not only a minefield, but because they are all designed to do different things and not talk to each other, security processes can become slow and complicated.
When considering an integrated email security package, look for one that can protect against malware as well as spam, phishing, potential data leaks and more!
The SonicWall email security and sensitive data detection solution can help. Deployed as a software or virtual appliance, this security system gives you complete peace of mind that your computer and operating system are protected.
7. Advanced internet protection technique

In this final chapter, we want to let you in on some of our tips and unique techniques over the years to increase the security of your computer.
Tips that we've never shared before.
7a) Keep things up to date!
Now before you think, you've heard all of this before, and there is nothing left to say on the matter, give us a second!
Yes, when we say keep things updated, we're talking about things such as updating and keeping the latest version of Microsoft - and yes, we know not everyone likes it, but it will help to add another layer of security to your PC.
But, what we also mean is that it's also important to keep the more uncommon elements like your routers and Java up to date too.
Java is something that most of us don't really know to update in the first instance, let alone do this regularly, so it's important to know more about it.
In your start menu, search for Java, clicking and bringing up the Java Control Panel. Any updates and new updates will then be available by the click of a button in the bottom right-hand corner of the panel.
Within this section, we'd also recommend clicking on the security tab at the top and disabling, the Enable Java box.
Why?
Because this is notorious for vulnerabilities and opens up more opportunities and threats than adding additional security.
When it comes to routers, keep these up to date by changing passwords asap, and follow this up with disabling WPS, or Wi-Fi Protected Setup.
Why?
Because if we're 100%, honest WPS is really shaky on the security front!
7b) Change your controls
Most computers and PCs will automatically be set up with you as the administrator with admin privileges and the ability to access everything without question.
Herein lies the problem.
In your control panel, make sure to switch your privileges from admin to standard.
Why?
Because if a virus or piece of malware does accidentally find its way onto your PC, being set up as admin will give the invader the same privileges that you have, and you don't want that to happen.
7c) Keep some things to yourself!
In an era where 2.77 billion people around the world use social media, (an estimated 2.77 billion people around the world use social media), we tend to give too much away about ourselves, our family, and our lives in general.
Stop.
Let's keep some things under wraps, as not placing yourself in a vulnerable position will only strengthen your security position when online fraud and identity theft occur.
7d) Quick-fire tips
Make sure your antivirus software offers real-time protection.
Be aware that even the most trusted websites can be compromised.
Back up everything. Using both local and online backup systems. and
Sign out of things before closing everything down!
Conclusion
Computer invaders are not going away, but being armed with the right tools and information can keep you and your PC protected.
If you enjoyed reading this guide, please feel free to share and comment below with any questions or insight you might have when it comes to computer invaders; we'd love to hear from you.











