How to create a professional cold email without going to recipients spam folder - The Ultimate Guide
How to create a professional cold email without going to recipients spam folder - The Ultimate Guide

At some point in our career lifetime, we have sent out or indeed been sent a cold email.
Those emails where there is no relationship as such with the sender, and you are introducing yourself for the first time. Cold emails are still to this day, the most effective way for businesses to increase their lead generation.
But, and there is a bit, these emails need to get through the numerous security filters and settings that businesses now operate.
Sometimes, you can have the world's best content inside those emails, but ultimately it comes down to whether your email will be a success or a failure.
Many things now need to be considered when sending out cold emails and this guide will show you not only how to create an expert cold email, but how to make sure it doesn't end up in the spam folder of the recipient.

Contents Covered
1. A guide to cold emailing
a. How to successfully land in someone's inbox
b. The most important dos and don'ts for cold emailing
c. Tips for producing compelling content
2. Cold emailing deliverability
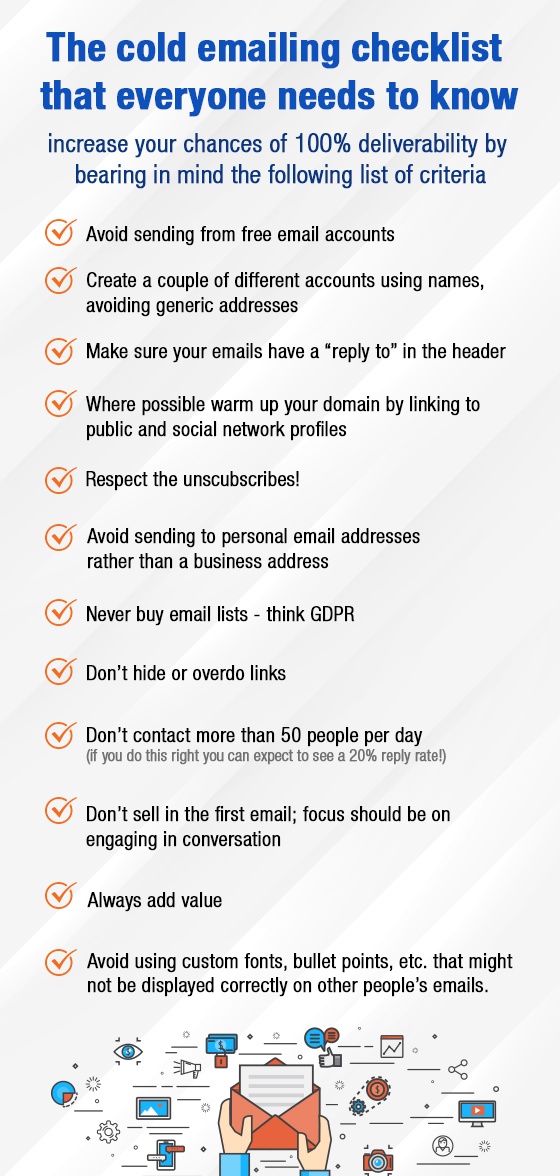
d. The cold email checklist everyone needs to know
3. Red flag
e. Need to show them you're human
f. Avoid similar content
g. Spam filters pay attention to things out of the ordinary.
h. No groups, only individuals
4. Spam emails
5. Your ultimate email security guide
6. Technical attacks
i. Viruses
j. Phishing attacks
k. Denial of service
7. Email encryption
l. The benefits
m. Encryption should be...
1a. A guide to cold emailing and how to successfully land in someone's inbox
There is no definitive way to successfully land in someone's inbox and make them read your email and then act upon its content.
But, in this chapter we will explore some of the tried and tested tips which can increase your chances of making this cold email a more successful one.
Starting with, make it personal. Most marketers and content writers will stress this in all sales approaches, but to make it clear, you need to tailor the message to the person you are sending it to to be successful.
Of course, this is harder than usual as you have no relationship with this person or feedback, etc, but it can be done. Research them, check out their LinkedIn profile, what interests them, what news is the following, how do they see the specific niche that they are specialising in, and what is it that they want?
You need to show them that you have put the work in. Make them feel special and not part of a cold emailing campaign where everyone has received the same message. Tell them why you are emailing them as opposed to anyone else, where do they fit in with your thinking etc.
Tell them about yourself. No boasting here, but you need to show them that you're credible and that they can trust you. Do you have any direct connections or mutual friends, similar groups that you are part of, etc.? The aim here is to make it, so you don't feel like a stranger to them. Remember we're told from a very young age not to talk to strangers, so you need something compelling to change this.
Identify their pain points and give them something they want. Why should they care about your email? What are their pain points? Make them appropriate and relevant to your content and the offer that you are providing them with.
Keep emails to the point and actionable. Research has shown that short emails are more likely to be read than long ones. People who ask for specific action will also get a higher response rate.
If you have a point in the email, get to it. And if you want the recipient to do something, tell them what that is. Try to avoid getting them to choose as this involves thinking and processing, which consumes too much time.
Say thank you. Being appreciative as well as showing a little bit of vulnerability provides recipients with the feeling that they're a good person if they help. Of course, it also gives them power and status too.
Finally, don't use templates and write the email as if you were giving a speech. If the email when read aloud doesn't flow smoothly, then change it.
1b. The most important do's and don'ts for cold emailing
For your email to be perfect 100% of the time, there are a few dos and don'ts to take into consideration when constructing your approach.
Do
- Target smartly: don't just email anyone, focus on whom you want to connect with, building a lead list and an understanding of your audience.
- Segment! You will be guaranteed to receive a higher click-through rate if your target audience is segmented appropriately, customising your pitch. (Look to segment by industry, title, location, company size, products of interest, etc.)
- Have a compelling subject line. This is the reason why they choose to open it or not. It should convey a fantastic benefit or spark some curiosity. Short to the point and ideally five words and under.
- Use the right sender name. Make sure to send the email from an actual person, not marketing@ for example; you will receive a much higher click-through when its person led.
- Split test everything. Test the length of your emails, the Call to Action, colours used, times sent, subject lines, how links are formatted, tone of voice, tracking links and more!
Don't
- Include too many pictures. Look to abide by the 80: 20 rule when it comes to text to picture ratio, especially as spammers are known to hide links in pictures, hence most security filters will reject emails with too many!
- Rush to close your prospect. Remember, they don't even know you. You need to build up trust and a rapport, dig deep, build a relationship and then go for the sale kill.
- Send all your cold emails all at once. This will only have them targeted as spam, pacing them at 20-30 second intervals between every send helps to avoid this trap.
- Forget to follow up. Reports show that 80% of sales require at least five follow-ups after initial contact. However, 92% of sales reps report to give up before then, with the 8% that carry on following up, closing 80% of sales.
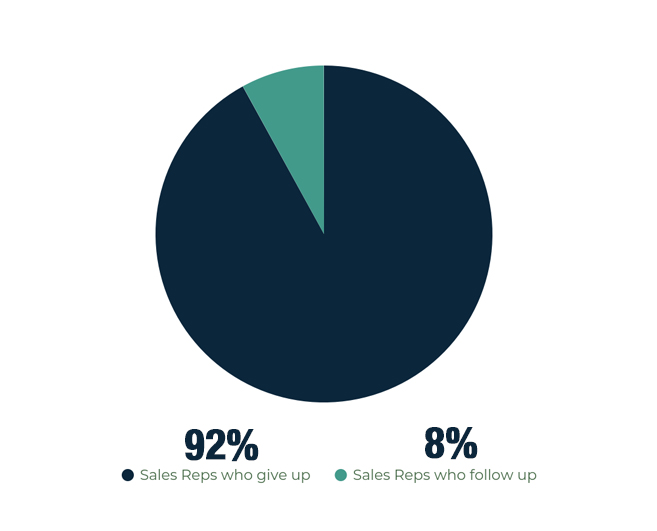
- Make follow-up emails generic. Make sure to inject a bit of humour where possible and keep things light-hearted; remember you're looking to build rapport.
- Track links. Tracking links within emails will increase your chances of hitting people's spam filters.
1c. Tips for producing compelling content
Content is what sells people, products, places, services and more. It's what we use to engage audiences with and get them to follow through on what we want them to do. This section looks at some top tips when it comes to creating such compelling content.
Mentioned earlier in this guide, is the point that within cold emails you need to communicate that you understand their pain points, and what you're going to tell them will help alleviate this, and what problems they/ there sector is facing.
Reminding them about the problems compels readers to read on, as they find common ground with someone who knows and shares their pain.
In some cases, research on cold email content has shown that if you raise these issues a little further, then swoop in with a solution, a positive result is more likely to follow-up with a call to action.
However, make it their decision. Make sure that they know that they are in charge. For example, if you would rather not, I fully understand and thank you for taking the time to read this email so far. This type of psychology doubles the chances that they'll say yes!
Content creation is about telling a story with a successful outcome at the end. You want to grab their attention, engage their interest, build a desire for your products and services by telling them about the facts, your big ideas, and the proof points. You ask them for a direct response, and you hook them with a strong call to action.
You will find that the most successful cold emails are fact-packed ones, those that are concise, specific, contain few adjectives and overall spark curiosity.
In a switched-on digital world, no one has time any more, so you need to make sure you get to the point.
We're not re-inventing the wheel, but instead using combinations of tried and tested formulas within our business contexts.
2. Cold emailing deliverability
Writing compelling content for an email to be read is one thing. Making sure it is delivered into the intended recipient's inbox is quite another.
With email security higher than ever, how can you ensure your emails are delivered correctly?
Firstly, and one which not many people are aware of, don't the very first cold email using your primary domain. Make sure to purchase a few domains that relate to your primary address, for cold email campaigns. This way, spam filters will not find your primary address.
It's also recommended that you avoid using.com where possible as these are also email addresses that are more likely to be checked by security software.
Secondly, check your email list. When 6-8% of the emails you send start bouncing, it will affect your overall email deliverability, with email providers soon blacklisting you across different platforms (see why we recommended buying alternative domains at the very beginning).
Check the details you have and the data you house, as well as monitor the bounce back rate when you start receiving emails in return.
Thirdly, you can check your deliverability using services such as mail-tester.com, taking their recommendations and working with the results you are then sent.
3. Red Flag
So, what constitutes a red flag when it comes to cold emails? What factors do they raise and how can we overcome them?
3.a. Need to show them you're human!
This is important, because email security software and spam filters can be very tight. If your email is thought to be spam, it will go through spam filters and never reach its intended destination.
A red flag in this area is when emails are all sent at the same time, without the time lag in between, this can show you as a spamming machine rather than a human being.
Make sure to pace your emails with 20-30 seconds between each send. Tools such as Mix max, Yesware, and Mail shake can all make it easier to send cold emails. They also give you advice on how to make your emails work better. (These platforms can also generate sending out emails through your Gmail accounts too).
3b. Avoid similar content
All content in your emails should be unique, but we tend to take advantage of commonly used words and phrases in the industries we work in.If you are sending out cold emails similar to content that is already out there or indeed like the content you have already sent (think about your follow-up emails), this will be followed-upgged and end up in spam folders or deleted altogether before even being read.
The key is not to repeat yourself; create unique and compelling content.
3c. Spam filters pay attention to things out of the ordinary
Things like additional links in the text or hidden in pictures. They also raise a red flag for shortening links.
In this case, it's important to write links in your email without making them a clickable link, or indeed disable link tracking systems. This will make it much easier to pass through spam filters.
3d. No groups, only individuals
Make sure when checking your email lists there are no group email addresses mixed up in there. Things such as finance@, sales@, etc as emailing these will again raise red flags and report your domain address as spam for any future communications.
4. Spam emails
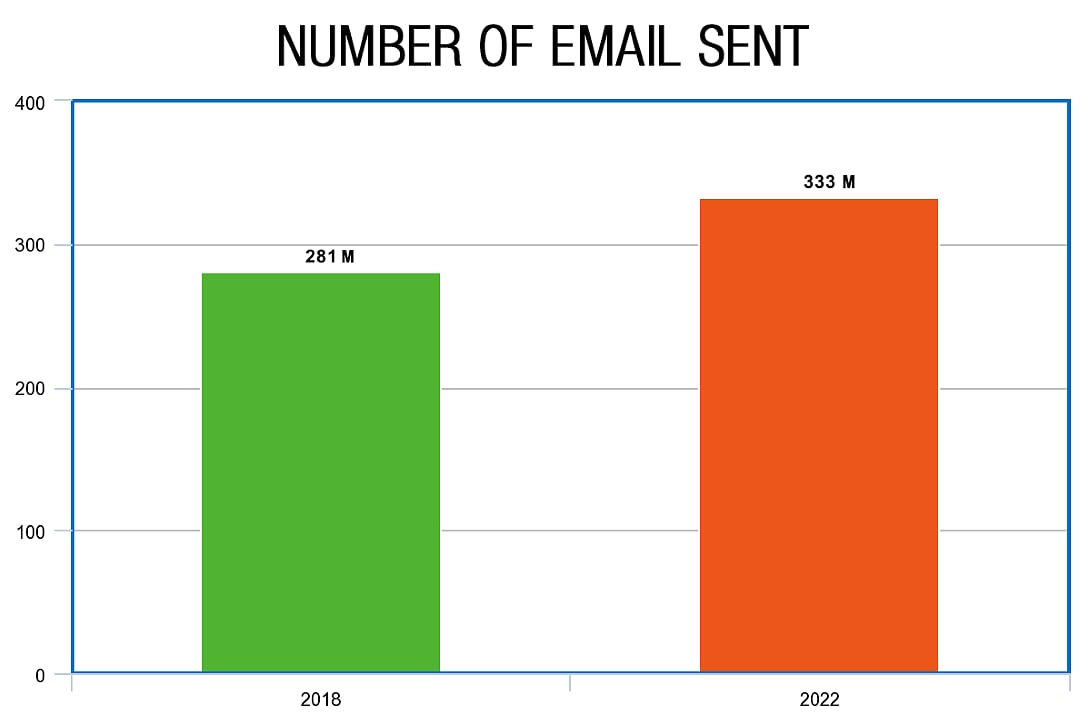
With studies showing that over 281 billion emails were sent in 2018 and about 333 billion could be sent in 2022, email plays an important role in business and society.
Knowing how email works is ultimately how we develop our understanding of spam emails as well as being aware of potential threats and IT attacks.
Email is ingrained in how we communicate, sell, inform, and develop. Offering us the opportunity to communicate with anyone, anywhere at any time. They are simple in nature, so everyone who encounters them understands how to use them.
However, messages and information are openly exposed to others and just because we can't physically see it doesn't mean this exposure isn't happening.
For example, emails can be intercepted, read, edited or even have viruses and malware placed within them, before being passed on to their final recipient.
For example, public networks mean just that!
Sending mail via public networks means that an email is visible to anyone. It goes through other people's servers to get to where it is going, and the people who run these servers can quickly stop it, do something with it, and then send it on its way.
The temptation of knowing what is sent in an email is too much for hackers; the temptation of knowing what is sent in an email is too much and placing something untoward in the email causing problems to the recipient.
5. Your ultimate mail security guide
There is a growing threat of hackers, viruses, spam emails, identity theft and phishing, as the number of people using email has increased dramatically.
So, how can you secure your business and keep your information safe?
Email security
When it comes to email security software and systems, this is often multi-layered, with several types of security technology now available.
Using things like spam filters, software that can scan email attachments (9 out of 10 viruses that infect a computer and network come from attachments), as well as relying on resources such as Microsoft eExchangeserver hosted encryption, can all help to increase email security. For example, Sophos PureMessage for Microsoft Exchange can scan all email messages.
Good network security systems
Private network security systems within the business increase email security as well as check for spam and phishing emails coming in through a secure server.
It's important to consider introducing instant messaging protection, email spyware protection, personal firewall tools (some of which will come with operating systems and then with add-on security suites), as well as identity protection and content blocking, which helps to prevent viruses and malicious content from getting into the computer system.
Good communication and training
Communicating and training staff in email security is key. Knowing what to look out for, and the signs of an unsolicited and potential spam email, is essential to embedding into the company culture.
Building email policies and best practices to include things such as:
- Don't open emails from unreliable sources
- Don't click on web links within emails
- Be careful when clicking on reply all within emails, as well as using the forward function
- Make use of the bcc
- Have strong passwords, which are never shared and updated regularly
Make sure you have the appropriate compliance controls in place so that you meet the legal and regulatory compliance requirements surrounding emails and email security.
6. Technical attacks Viruses
Viruses come in many forms and from several different sources, affecting computers and systems in different ways. Viruses are a way to install malware or malicious software onto your computer to delete information, steal data and information, even hold information and you hostage!
Time-consuming and annoying, viruses can take a painstaking process for them to be entirely removed from your machines and networks.
The best way to counteract viruses is to include anti-virus filters, filters which remove infected and potentially infected emails from the system before an employee even has a chance to open it, let alone click any links or attachments.
6b. Phishing attacks
Phishing attacks are a way for hackers and spammers to target users to try and get them to hand over and enter personal details. Usually entered onto a fraudulent site, phishing emails are much more sophisticated now than a couple of years ago, looking authentic in appearance and with many passing through email security and antivirus settings.
It's important to look at your email filtering services and train employees on how to spot a potential phishing attack and what to look out for in a phishing email.
Protecting customers, employees and your business from the latest phishing attacks out there is vital to protecting your personal and company data.
6c. Denial of service
This is independent of human error and designed to overload the company's mail server with incoming mail and attachments. A DoS attack is both an inconvenience and time-consuming; however, if it does happen, it's important that you base your email security over multiple data centers.
7. Email Encryption
Email encryption is used to protect sensitive information sent in emails. Encryptions services can help protect both the sender and the recipient. Depending on the type of encryption used, it can be very difficult to break because the code is very complex.
7a. Benefits of email encryption
Mitigates risk
Human error is inevitable. Sharing information publicly when it's a private document, forwarding the wrong email to the wrong person, and sharing attachments that shouldn't be shared are all bad for your business.
Using encryption software helps to mitigate these risks and problems, as it allows you to control information much more carefully.
Control information contained within emails by being able to set time limits before emails automatically expire, disabling forward options so that emails can't be passed around, and having recall functions if emails are sent by mistake.
Controls access
You can control access at each stage of your email journey, showing who has access to your content, who has received it and if so who, etc.
Ultimately you are in control, and you can always remain in control.
Don't always have to remember
Integrating email encryption into your IT solutions can make sure that employees don't have to continually remember how to encrypt sensitive information or protect email attachments, as this will be done for them as part of their operating system and they will not have to remember how to do it.
7b. Email encryption should
- Be effortless
- Be universal
- secure any file attachments
- transport sensitive information securely
- remain private!
Without email encryption, your email messages and attachments remain unprotected.
Conclusion
Cold emailing plays a vital role in business development and networking. Making the right email, with the right information, and using the right software approach can ensure that the email is actually read by the intended recipient, and not just spam.
If you have any questions you'd like to ask, maybe you'd like to share your email security experiences with us, or if you feel something is missing from our guide, we'd love to hear from you! Comment in the box below or email enquiries@sonicwall-sales.com
Read related post: Everything You Need to Know About Log4j








